How to Use Ghidra – Complete Beginner’s Guide
Reverse engineering has become an essential skill for cybersecurity experts, malware analysts, and software developers who want to understand how programs work under the hood. One of the most powerful tools for this purpose is Ghidra, developed by the National Security Agency (NSA). It is open-source, versatile, and packed with professional-grade analysis features. In this article, we’ll explore how to use Ghidra effectively, from installation to performing basic reverse engineering tasks.
What Is Ghidra?
Ghidra is a software reverse engineering (SRE) tool that allows users to analyze compiled code and understand its inner workings. It supports numerous architectures, such as x86, ARM, and MIPS, and is ideal for malware analysis, vulnerability research, and software auditing.
Key features include:
- Disassembler & Decompiler: Converts binary code into human-readable form.
- Graphical Interface: Simplifies complex code navigation.
- Collaboration Tools: Enables multiple analysts to work together.
- Extensibility: Supports plugins and Python scripting for customization.
System Requirements to Run Ghidra
Before learning how to use Ghidra, ensure your system meets the following requirements.
| Specification | Minimum Requirement | Recommended Requirement |
|---|---|---|
| Operating System | Windows 10 / Linux / macOS | Windows 11 / Ubuntu 22.04 |
| RAM | 4 GB | 8 GB or more |
| Processor | Dual-core CPU | Quad-core or higher |
| Java Version | JDK 17 or newer | Latest OpenJDK build |
| Disk Space | 1 GB (for setup) | 2+ GB for large projects |
Step 1: Downloading and Installing Ghidra
To start, visit the official Ghidra website (ghidra-sre.org) and download the latest version. The tool is distributed as a ZIP file, so you don’t need to run an installer.
Installation steps:
- Extract the downloaded ZIP file to your preferred location.
- Ensure Java JDK 17 or above is installed.
- Open the extracted folder and double-click ghidraRun.bat (on Windows) or ghidraRun (on Linux/macOS).
- The Ghidra interface will launch, displaying the Project Manager window.
Step 2: Creating a New Project
Once you’ve opened the application, follow these steps:
- Click File → New Project.
- Choose Non-Shared Project (or Shared if collaborating).
- Name your project and select a storage directory.
- You can now import executable files such as
.exe,.dll, or.bin.
This will be your workspace for analyzing and experimenting with binaries.
Step 3: Importing and Analyzing a File
Let’s move deeper into how to use Ghidra for practical analysis.
To analyze a file:
- Click File → Import File and select your binary.
- Ghidra will automatically detect the architecture.
- Once imported, double-click the file in the Project Manager window to open it in CodeBrowser.
- You’ll be prompted to Analyze the file — click Yes and configure the options (e.g., decompiler, function ID).
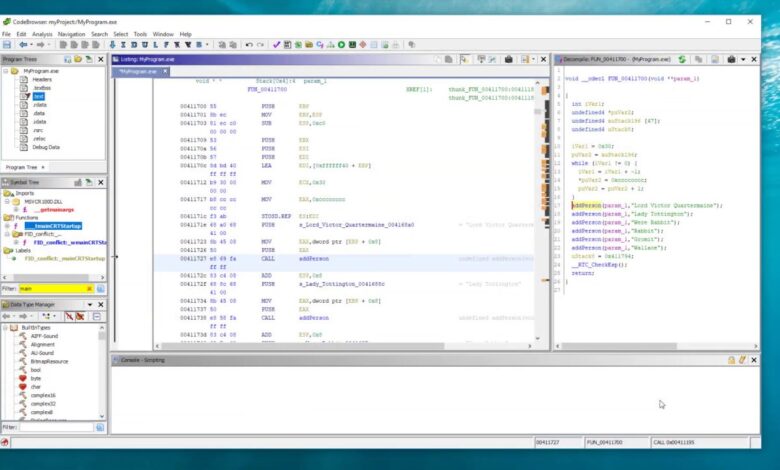
After the analysis, Ghidra will display a disassembled view and a decompiled pseudocode version. This allows you to understand the logic of the binary program even if you don’t have access to its source code.
Step 4: Navigating the Interface
The Ghidra interface is divided into several key sections:
- Listing Window: Shows disassembled assembly code.
- Decompiler Window: Displays high-level pseudocode.
- Symbol Tree: Lists functions, variables, and labels.
- Data Type Manager: Manages data structures and memory layouts.
You can navigate between functions, rename variables, and even comment on code segments for clarity. This makes reverse engineering structured and easier to interpret.
Step 5: Decompiling Functions
Ghidra’s decompiler is one of its most powerful features.
To decompile a function:
- Click on any function name in the Symbol Tree.
- The decompiled C-like code will appear in the Decompiler window.
- You can rename variables, adjust data types, or explore cross-references using the right-click menu.
This functionality helps malware analysts and developers understand unknown or obfuscated code.
Step 6: Using Scripts and Plugins
Another reason experts love how to use Ghidra workflows is the flexibility through scripting.
Ghidra supports Jython (Python for Java) and Java scripts.
You can automate tasks like:
- Batch analysis of multiple binaries.
- Detecting specific functions or patterns.
- Exporting analysis results.
To access scripts, go to:
Window → Script Manager → New Script
You can write or edit scripts to fit your analytical goals.
Step 7: Collaboration and Version Control
For teams, Ghidra offers Shared Projects, which store project data on a shared repository.
Analysts can work simultaneously, commit changes, and track versions.
This feature is vital for organizations conducting large-scale vulnerability assessments or joint malware analysis operations.
Benefits of Using Ghidra
| Feature | Benefit |
|---|---|
| Open-source | Free to use and customizable |
| Multi-platform | Works on Windows, macOS, and Linux |
| Decompiler | Converts assembly into readable code |
| Collaboration | Team-based project support |
| Extensible | Supports plugins and scripting |
| Supported Architectures | x86, ARM, MIPS, PowerPC, etc. |
Common Use Cases
- Cybersecurity Training: Teaching students how binary programs work.
- Malware Analysis: Understanding malicious code behavior.
- Software Debugging: Fixing issues in closed-source applications.
- Vulnerability Research: Finding and patching security flaws.
Tips for Efficient Use
- Always keep your Java version updated.
- Regularly save your project progress.
- Use the Bookmarks feature to mark important code sections.
- Combine Ghidra with tools like IDA Free or Binary Ninja for broader insight.
Conclusion
Learning how to use Ghidra can open doors to an exciting world of reverse engineering, software auditing, and cybersecurity research. With its advanced decompilation engine, multi-architecture support, and open-source flexibility, Ghidra empowers analysts to dive deep into binary code safely and efficiently.
Whether you are a cybersecurity student or a professional malware researcher, mastering Ghidra’s interface, features, and scripting capabilities can significantly elevate your analytical skills.
FAQs
1. Is Ghidra free to use?
Yes, Ghidra is completely free and open-source, released under the Apache 2.0 license.
2. Who developed Ghidra?
It was developed by the U.S. National Security Agency (NSA) and made publicly available in 2019.
3. Can Ghidra analyze any file type?
It supports a wide range of executable formats, including ELF, PE, and Mach-O.
4. Does Ghidra require programming knowledge?
Basic programming and assembly understanding help, but beginners can still use it effectively due to its intuitive GUI.