Reverse engineering has become an essential skill for cybersecurity experts, malware analysts, and software developers who want to understand how…
Read More »Admin
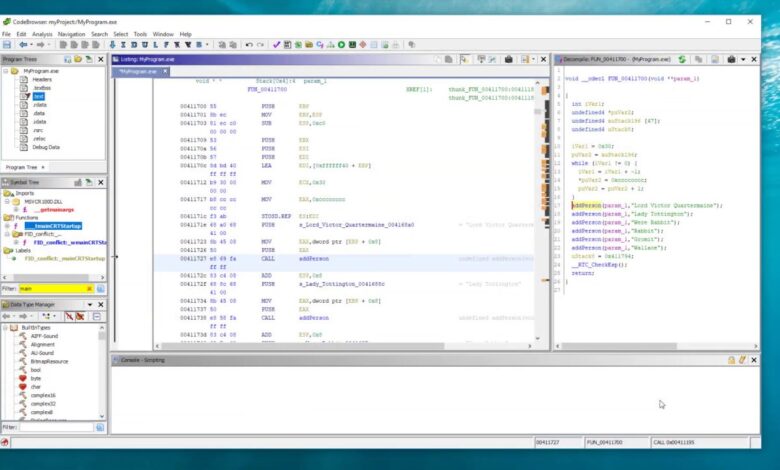
Introduction Cybersecurity professionals, ethical hackers, and software engineers constantly require robust tools to analyze software, uncover vulnerabilities, and ensure digital…
Read More »Introduction In the modern cybersecurity landscape, reverse engineering tools play a critical role in understanding how software behaves. Whether analyzing…
Read More »Ghidra is a robust, open-source reverse engineering platform developed by the NSA (National Security Agency) and released publicly in 2019.…
Read More »The integration of edge computing with artificial intelligence is poised to redefine operational frameworks across various sectors by 2025. This…
Read More »The transition from classical to quantum computing signifies a pivotal shift in computational capabilities. Classical systems rely on bits, processing…
Read More »The rise of automation has initiated a profound shift in the workplace, transitioning from mere task execution to a collaborative…
Read More »The emergence of cloud-native applications signifies a crucial evolution in software development practices. Organizations are increasingly adopting microservices, containerization, and…
Read More »Zero Trust Security represents a paradigm shift in cyber defense strategies. By prioritizing continuous verification and strict access controls, it…
Read More »